Riot Games’ free-to-play FPS Valorant has come under fire for their anti-cheat software, which some claim give them access to spy on users even when the game is not running.
The closed beta for Valorant launched on April 7th. On April 14th Riot Games posted a blog post discussing the game’s anti-cheat measures. Therein, they revealed the game was using a kernel driver for their anti-cheat software, in a post they had detailed two months earlier. Valorant would be the first Riot Games game to use the new anti-cheat software.
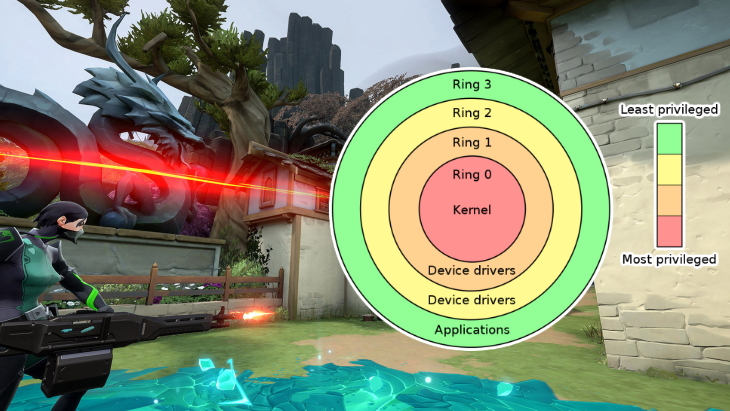
A kernel, in extreme layman terms, is part of the computer’s operating system. It allows hardware such as CPU, memory, and devices, to interact with software and applications.
Riot Games state that installing anti-cheat software at the kernel-level can help counteract cheating software operating at a similar level. “The problem here arises from the fact that code executing in kernel-mode can hook the very system calls we would rely on to retrieve our data, modifying the results to appear legitimate in a way we might have difficulty detecting.”
At the end of their earlier blog on the kernel-based anti-cheat software, they also explained why users should not panic.
- “Stress can lead to excess hair loss, and I don’t want your head to get cold.
- This isn’t giving us any surveillance capability we didn’t already have. If we cared about grandma’s secret recipe for the perfect Christmas casserole, we’d find no issue in obtaining it strictly from user-mode and then selling it to The Food Network. The purpose of this upgrade is to monitor system state for integrity (so we can trust our data) and to make it harder for cheaters to tamper with our games (so you can’t blame aimbots for personal failure).
- This isn’t even news. Several third party anti-cheat systems—like EasyAntiCheat, Battleye, and Xigncode3—are already utilizing a kernel driver to protect your favorite AAA games. We’re just installing our own sous-chef to the Windows kitchen, so that when we hit em with a ‘where’s the beef,’ we know we’re getting an honest answer.
- It will be significantly harder to create undetected cheats: protecting you from aimbots, protecting us from Reddit, and protecting cheaters from themselves.”
Some in the comments of the Valorant blog post showed concerns about the security and privacy of installing the anti-cheat software at kernel level, as did OS News.
They claim that the anti-cheat software would give Riot Games the ability to see all activities a user performs on their computer, even when the game is not running.
“Valorant is their first game using this kernel driver, and as it turns out, this kernel driver starts at boot, and due to its very nature has full system access, even when you’re not running Valorant.
According to Riot Games, we just have to trust them on their blue eyes that their kernel driver is fully secure and won’t be exploited by malicious third parties, and that the company won’t use it to spy on people or otherwise violate their privacy. Riot states on Reddit that ‘multiple external security research teams’ have reviewed the driver, but as far as I can tell, these reviews have not been published for public vetting.”
As mentioned above, Riot Games’ Anti Cheat Lead Paul Chamberlain took to Reddit when the concerns were first brought up, denying the program would spy on users, or collect data.
“TL;DR Yes we run a driver at system startup, it doesn’t scan anything (unless the game is running), it’s designed to take up as few system resources as possible and it doesn’t communicate to our servers. You can remove it at anytime.
Vanguard contains a driver component called vgk.sys (similar to other anti-cheat systems), it’s the reason why a reboot is required after installing. Vanguard doesn’t consider the computer trusted unless the Vanguard driver is loaded at system startup (this part is less common for anti-cheat systems).
This is good for stopping cheaters because a common way to bypass anti-cheat systems is to load cheats before the anti-cheat system starts and either modify system components to contain the cheat or to have the cheat tamper with the anti-cheat system as it loads. Running the driver at system startup time makes this significantly more difficult.
We’ve tried to be very careful with the security of the driver. We’ve had multiple external security research teams review it for flaws (we don’t want to accidentally decrease the security of the computer like other anti-cheat drivers have done in the past). We’re also following a least-privilege approach to the driver where the driver component does as little as possible preferring to let the non-driver component do the majority of work (also the non-driver component doesn’t run unless the game is running).
The Vanguard driver does not collect or send any information about your computer back to us. Any cheat detection scans will be run by the non-driver component only when the game is running.
The Vanguard driver can be uninstalled at any time (it’ll be ‘Riot Vanguard’ in Add/Remove programs) and the driver component does not collect any information from your computer or communicate over the network at all.
We think this is an important tool in our fight against cheaters but the important part is that we’re here so that players can have a good experience with Valorant and if our security tools do more harm than good we will remove them (and try something else). For now we think a run-at-boot time driver is the right choice.”
One of OS News’ concerns, comparing Vanguard to rootkits, include how similar software had been exploited by hackers in the past- even if the company itself has no malicious intentions.
They cite the Sony BMG copy protection rootkit scandal, where Sony CDs installed copy protection software onto PCs without the user’s consent. This program became exploited by hackers to inject malware, and attempts to uninstall the program were difficult (with official uninstallers only hiding the program).
They also cited incidents with anti-hacking rootkits introduced in Street Fighter V, which were quickly rolled back after public outcry, and Riot Games’ own League of Legends allegedly installing a crypto-currency miner into Filipino versions of the game.
Another element that OS News is concerned about is Riot Games being wholly owned by Chinese tech giant Tencent. Due to Tencent complying with government regulations on providing personal information of users on their messaging platform WeChat, OS News considers them “for all intents and purposes, an arm of the Chinese government.”
“So not only do you have to trust Riot Games,” they propose, “you also have to trust their owner, Tencent, as well as who Tencent literally answers to – the Chinese government.”
“Players of Riot’s games will have to ask themselves if they trust Riot to install a rootkit with complete and full access to their system,” OS News state. “Browsing history, chat logs, email, everything. You have to trust Riot when they say the rootkit is ‘secure’ and won’t be exploited by malicious third parties, and that the company itself won’t use it to invade your privacy.”
When independent security researcher Saleem Rashid spoke to Ars Technica on the matter, he stated the system could be more at risk of crashing from bugs, or use exploits such as buffer overflow.
“Whenever you have a driver like that, you’re at risk of introducing security and reliability issues to the computer. You don’t get as many exploit mitigations in device drivers as you do in normal applications, and a bug will crash the entire OS, not just the game.
DRM like this probably stops cheating in the very near term, but I’m not convinced it helps in the long run. All it takes is for someone to analyze the driver from outside of Windows and then apply similar techniques they use to defeat other anti-cheat systems. So it looks like it introduces a large attack surface for little benefit.”
Chamberlain elaborated on his earlier Reddit post to Ars Technica in an email. “The primary responsibility of the kernel driver is to create a protected environment for the rest of Vanguard (and the game) to operate in. If the integrity of the anti-cheat system is ensured, then almost everything else can happen entirely in user-mode.”
He also reiterated that Riot Game’s Application Security team was (in Ars Technica’s words) “aided by the services of three separate external security groups to audit Vanguard before it was rolled out. That includes one group that was focused exclusively on the driver and another that performed ‘black box’ attacks on the system from the outside.”
Chamberlain stated that Vanguard has “code integrity checks and crash reporting functionality” to warn Riot Games of any issues. “In addition,” Chamberlain stated, “we have our bug bounty program and good relationships with the game security community and the broader threat intelligence community, so we would be well placed to receive intelligence about potential compromises.”
If a “kernel-mode code execution bug” was discovered in Vanguard’s drivers, Chamberlain claims the system is set up “to be easy to update on whatever cadence is required (separate from game update cadence) so we would likely be able to respond within hours.” During that time, Vanguard would be disabled, and players would be told to uninstall it.
“In extreme cases, we would work with our patcher team to automatically remove Vanguard from all players’ computers,” Chamberlain stated. “After we had pushed a fix or removed the driver, we would work with Microsoft to get the vulnerable driver blacklisted.”
What do you think? Do you trust anti-cheat software at the kernel level? How would you deal with cheaters? Sound off in the comments below!
Image: Valorant official website, Wikipedia